Every computer has a unique IP address with encrypted information about the user’s geolocation and ISP. Proxy servers also have IP addresses. If a user accesses the Internet through a proxy, the IP of a proxy is shown while a user can remain incognito. You can buy eu proxies at a bargain price on soax.com, and we will tell you more about this technology.
What is a proxy server used for?
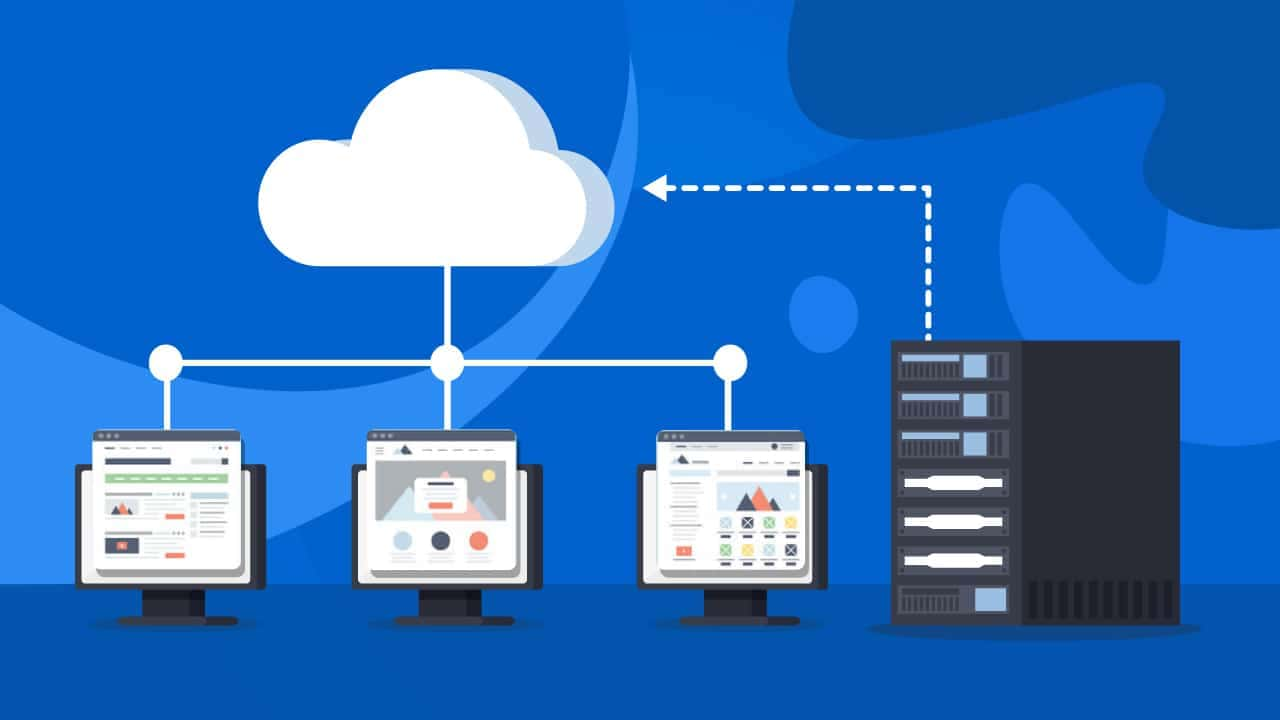
A proxy is a part of theInternet connection that connects the user’s device and the resource server. The purpose of this intermediary remote computer is to receive and forward requests from a user who needs to access the Internet but doesn’t want their computer to access directly to the site. A proxy server does the following:
- provides confidentiality of data;
- makes the Internet connection safe by protecting the computer from network attacks;
- allows you to use the content available only in a specific location;
- allows you to connect multiple computers from a single IP address;
- makes blocked online resources available.
Remember that the owner of a proxy server can see all the web traffic going through the proxy. You should decide whether to trust this owner or not.
How does a proxy connection work?
Every device connected to the Internet has a unique IP address to identify a user. An IP address consists of a network number and a node number. An IP identifies a country, region, ISP, and PC belonging to the provider’s network. Proxy servers also have unique IP addresses.
When a computer connects to a proxy and sends requests to the Internet, the IP address of this proxy server is defined while a user can remain incognito. To connect to the proxy, you should configure the browser’s settings.
A provider connects a user’s device to a remote server and then to a blocked resource or spoofs an IP address. An IP address is then determined as a proxy server’s address. When a user goes to any site, their computer connects to a proxy and makes a request. If a request is valid, a response reaches a computer and connects it to a site.
Why is IP spoofing needed and what is it used for?
People use proxies to spoof their IP for various reasons, e.g. to avoid being blocked by IP or to remain unrecognized on the Internet:
- Internet resources see an IP address and find out where the user’s computer is, so there is no privacy and security;
- content may be blocked by IP address, using the geolocation of a computer or another device.
However, IP spoofing can also be the direction of a hacker attack when an IP is used to trick the security system to get into a certain computer network. Such actions are called IP spoofing. A hacker uses someone’s IP to access the desired data.